Wednesday, December 16, 2009
Restore Icons to the Desktop
1. Right-click the desktop and click Properties.
2. Click the Desktop tab.
3. Click Customize desktop.
4. Click the General tab, and then click the icons that you want to place on the desktop.
5. Click OK.
Thanks Microsoft.
Sunday, December 13, 2009
How to set path using bat file
cmd /k "set path=%path%;"c:\Program Files\Java\jdk1.5.0\bin"&&z:"
Tuesday, December 8, 2009
Time synchronization between server and client
This command is used in client computer.
w32tm /resync /computer:computername or domainname /nowait /soft
Tuesday, December 1, 2009
avoid anonymous connections using Group Policy Objects
What you are protecting
Once an attacker has made an anonymous connection to your computer, gaining access to much of the security-related information is easy. An attacker can gather the following information with an anonymous connection:
- List of users from your computer, including Active Directory
- List of groups from your computer, including Active Directory
- Security identifiers (SIDs) for user accounts
- User accounts for SIDs
- List of shares from your computer
- Account policies from your computer
- NetBIOS name from your computer
- Domain name associated with your computer
- List of domains that your domain trusts
Protection-level updates are here
To protect against anonymous connections and enumeration of essential security information, you should use Group Policy Objects. Microsoft changed the level of protection for the Windows 2000 and Windows XP/2003 environments.
- Network access: Allow anonymous SID/Name translation. This protects against tools that can grab the SID based on a name or vice-versa. You should set this to "Disabled."
- Network access: Let Everyone permissions apply to anonymous users. This protects against an anonymous connection accessing all resources that the Everyone group is configured to access. You should set this to "Disabled."
- Network access: Do not allow anonymous enumeration of storage area management (SAM) accounts. This protects against enumerating the list of users and groups in the SAM directory (or Active Directory). You should set this to "Enabled."
- Network access: Do not allow anonymous enumeration of SAM accounts and shares. This protects against listing users and groups from the SAM directory, as well as the list of shares for the computer. You should set this to "Enabled."
Monday, November 23, 2009
IE Content Advisor to block all Internet access
1. Copy the following text into Notepad and save it as “noaccess.rat” in the Windows\system32\ directory (or another directory of your choice). Be sure that the file extension is .rat and not .txt.
((PICS-version 1.0)
(rating-system “http://www.microsoft.com”)
(rating-service “http://www.microsoft.com”)
(name “Noaccess”)
(description “This file will block all sites.”)
(category
(transmit-as “m”)
(name “Yes”)
(label
(name “Level 0: No Setting”)
(description “No Setting”)
(value 0))
(label
(name “Level 1: No Setting”)
(description “No Setting”)
(value 1))))
2. In the “Control Panel” double-click on “Internet Options” and click on the “Content” tab. If in Internet Explorer, click on “Tools” and “Internet Options” and click on the “Content” tab.
3. Click “Enable.”
4. Inside the “General” tab click on “Rating System.”
5. Remove all entries and click “Add.” Add “noaccess.rat” from the Windows\system32\ directory.
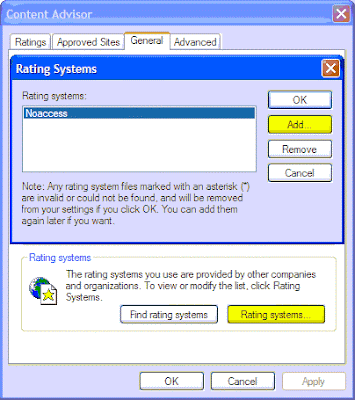
Content Advisor Block Internet
6. Click on the “Approved Sites” tab and add all the websites you wish to allow access to.
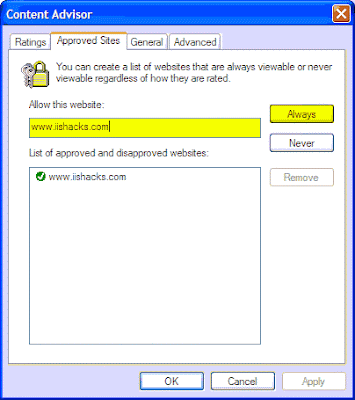
content advisor configuration throw GPO
Content Advisor as a "white list" in a Group Policy Object (GPO) for Windows
XP PCs. Note: White list refers to blocking all internet access except for
selected sites (deny all, except).
1. Microsoft Active Directory (AD) does not have an option to simply
enable the Content Advisor. Instead, they use a model of importing settings
from the computer on which the AD Group Policy Object is being edited and
allowing you to configure those settings. So the first thing to do is to
enable the Content Advisor on the editing machine. If this is not done then
the Content Advisor configuration will be propagated out to the client
machines but the Content Advisor itself will not be enabled (turned on).
* Once the rest of this process has been completed, the Content
Advisor may be disabled on the editing machine with no effect to the clients
as just the importing of the settings is needed.
* Remember to enable the Content Advisor on the editing machine in
the future if changes are to be made to the Active Directory Group Policy
Object Content Advisor configuration to avoid inadvertently disabling the
Content Advisor on the target PCs.
1. Open IE and go to: Tools -> Internet Options
2. On the Content tab, under Content Advisor at the top, click the
button labeled "Enable". You will be prompted for the local machine Admin
password. Once this is done the button label changes to "Disable", thus
confirming that the Content Advisor has been turned on.
3. Click "OK" to exit Internet Options and close out of Internet
Explorer.
2. To make the "deny all", on BOTH the user PC and on the machine that
will be editing the Group Policy Object (again the importing) in
C:\WINDOWS\system32 create a text file named "noaccess.rat".
3. Use an editor to add the following:
((PICS-version 1.0)
(rating-system "http://www.microsoft.com")
(rating-service "http://www.microsoft.com")
(name "Noaccess")
(description "This file will block all sites.")
(category
(transmit-as "m")
(name "Yes")
(label
(name "Level 0: No Setting")
(description "No Setting")
(value 0) )
(label
(name "Level 1: No Setting")
(description "No Setting")
(value 1) ) ))
4. Save and Exit.
5. Open Group Policy Management (editing machine).
6. Locate the GPO in which you want to enable the Content Advisor.
7. Right click the object and select "Edit...".
8. In the now opened Group Policy Object Editor go to: User Configuration
-> Windows Settings -> Internet Explorer Maintenance -> Security
9. Double click on "Security Zones and Content Ratings"
10. Under "Content Ratings" click the radio button labeled "Import the
current Content Ratings settings" (the aforementioned importing step).
11. Click the button labeled "Modify Settings".
12. Enter the supervisor password and click "OK".
13. On the Ratings tab select the Noaccess category (this is the file that
was created earlier).
14. On the Approved Sites tab enter the list of approved sites, one at a
time, while selecting "Always" as "Never" was taken care of with the
noaccess.rat file.
* The wildcard * (asterisk) can be used to denote pages in a site
(eg. http://www.case.edu* for all of http://www.case.edu)
* Supposedly, the Content Advisor treats http requests as simply
www (eg. http://www.case.edu is treated as www.case.edu) but it's probably a
good idea to be as specific as possible to avoid confusion. Especially when
secure http (https) is a possibility.
* It may be a good idea to include the default homepage as
Internet Explorer may throw an error if the default homepage is content
restricted. This can be set with the Group Policy Object Editor. Go to: User
Configuration -> Windows Settings -> Internet Explorer Maintenance -> URLs.
Double click "Important URLs" and then check the box labled "Customize Home
page URL" and enter the desired site (eg. http://www.case.edu or about:blank
for a blank page).
15. On the General tab uncheck the box under User options labeled "Users
can see websites that have no rating".
* The other option is up to you as to whether to allow for an
Admin override prompt when blocked content is encountered.
16. On the Advanced tab remove any ratings bureaus.
17. Click OK twice and exit out of the Group Policy Object Editor
18. For the policy to take effect on a user's PC, the best thing to do
would be to simply reboot the PC. You can also type "gpupdate /Force" at the
command line with Admin privileges.
* The PC has to be in the Organizational Unit (OU) to which the
GPO applies.
19. Don't forget to test BEFORE deployment. Even after. And later on...
----
If you’re using IE7, please try to install the following hotfix.
The Internet Explorer Maintenance Group Policy settings for the Content Advisor do not work on client computers that have Internet Explorer 7 installed
http://support.microsoft.com/kb/950065
Also, to block website, it’s suggested to use other policy or method, such as Proxy, Firewall settings to block them completely. They are better choice than Content Advisor for this purpose.
Friday, November 6, 2009
Error message when you try to set an IP address on a network adapter
A network adapter with the same IP address is in the registry but is hidden in Device Manager. This can occur when you move a network card from one PCI slot to another PCI slot.
Method 1
- Click Start, click Run, type cmd.exe, and then press ENTER.
- Type set devmgr_show_nonpresent_devices=1, and then press ENTER.
- Type Start DEVMGMT.MSC, and then press ENTER.
- Click View, and then click Show Hidden Devices.
- Expand the Network Adapters tree.
- Right-click the dimmed network adapter, and then click Uninstall.
Method 2
The DevCon utility is a command-line utility that acts as an alternative to Device Manager. When you use DevCon, you can enable, disable, restart, update, remove, and query individual devices or groups of devices. To use DevCon, follow these steps:- Download the DevCon tool by clicking the following article number to view the article in the Microsoft Knowledge Base: 311272 (http://support.microsoft.com/kb/311272/ ) The DevCon command-line utility functions as an alternative to Device Manager
- Unpack the 32-bit or 64-bit DevCon tool binary to a local folder.
- Click Start, click Run, then type cmd and press ENTER.
- Type CD:\path_to_binaries to navigate to the devcon.exe is located.
- Use the following syntax to find installed network adapters:
devcon findall =net or
devcon listclass net
Note In the output of the previous commands, there is a line for the ghosted network adapter that is similar to the following:PCI\VEN_10B7&DEV_9200&SUBSYS_00D81028&REV_78\4&19FD8D60&0&58F0: 3Com 3C920 Integrated Fast Ethernet Controller (3C905C-TX Compatible) - Remove the ghosted device by typing the following syntax: devcon -r remove "@PCI\VEN_10B7&DEV_9200&SUBSYS_00D81028&REV_78\4&19FD8D60&0&58F0"
thanks Microsoft
Tuesday, September 22, 2009
How to disable USB device Via group policy
CLASS MACHINE
CATEGORY !!category
CATEGORY !!categoryname
POLICY !!policynameusb
KEYNAME "SYSTEM\CurrentControlSet\Services\USBSTOR"
EXPLAIN !!explaintextusb
PART !!labeltextusb DROPDOWNLIST REQUIRED
VALUENAME "Start"
ITEMLIST
NAME !!Disabled VALUE NUMERIC 3 DEFAULT
NAME !!Enabled VALUE NUMERIC 4
END ITEMLIST
END PART
END POLICY
POLICY !!policynamecd
KEYNAME "SYSTEM\CurrentControlSet\Services\Cdrom"
EXPLAIN !!explaintextcd
PART !!labeltextcd DROPDOWNLIST REQUIRED
VALUENAME "Start"
ITEMLIST
NAME !!Disabled VALUE NUMERIC 1 DEFAULT
NAME !!Enabled VALUE NUMERIC 4
END ITEMLIST
END PART
END POLICY
POLICY !!policynameflpy
KEYNAME "SYSTEM\CurrentControlSet\Services\Flpydisk"
EXPLAIN !!explaintextflpy
PART !!labeltextflpy DROPDOWNLIST REQUIRED
VALUENAME "Start"
ITEMLIST
NAME !!Disabled VALUE NUMERIC 3 DEFAULT
NAME !!Enabled VALUE NUMERIC 4
END ITEMLIST
END PART
END POLICY
POLICY !!policynamels120
KEYNAME "SYSTEM\CurrentControlSet\Services\Sfloppy"
EXPLAIN !!explaintextls120
PART !!labeltextls120 DROPDOWNLIST REQUIRED
VALUENAME "Start"
ITEMLIST
NAME !!Disabled VALUE NUMERIC 3 DEFAULT
NAME !!Enabled VALUE NUMERIC 4
END ITEMLIST
END PART
END POLICY
END CATEGORY
END CATEGORY
[strings]
category="Custom Policy Settings"
categoryname="Restrict Drives"
policynameusb="Disable USB"
policynamecd="Disable CD-ROM"
policynameflpy="Disable Floppy"
policynamels120="Disable High Capacity Floppy"
explaintextusb="Disables the computers USB ports by disabling the usbstor.sys driver"
explaintextcd="Disables the computers CD-ROM Drive by disabling the cdrom.sys driver"
explaintextflpy="Disables the computers Floppy Drive by disabling the flpydisk.sys driver"
explaintextls120="Disables the computers High Capacity Floppy Drive by disabling the sfloppy.sys driver"
labeltextusb="Disable USB Ports"
labeltextcd="Disable CD-ROM Drive"
labeltextflpy="Disable Floppy Drive"
labeltextls120="Disable High Capacity Floppy Drive"
Enabled="Enabled"
Disabled="Disabled"
----
Thanks Microsoft
Wednesday, September 9, 2009
Errors occurred while Windows was synchronizing your data
files through the domain group policy. However since its only one
machine thats got the problem I'd say its probably best to disable
offline files through the local group policy:
1. Start > Run > 'mmc'
2. File > Add/Remove Snap-in > Add > Group Policy > OK.
3. In the GP window; Comp Config > Admin Template > Network > Offline
Files.
Disable 'Allow or Disable use of offline files feature'
You may also want to disable 'Do not auto make redirected folders...'
in User Config > Admin Temp > Network > Offline Files.
Tuesday, August 4, 2009
PushPrinterConnections.exe file to startup or logon scripts
-
Open the GPMC.
-
In the GPMC console tree, navigate to the domain or organizational unit (OU) that stores the computer or user accounts where you want to deploy the PushPrinterConections.exe utility.
-
Right-click the GPO that contains the printer connections that you want to deploy using Group Policy, and then click Edit.
-
Navigate to one of the following locations:
- If the printer connections are deployed per-computer, go to Computer Configuration, Policies, Windows Settings, Scripts (Startup/Shutdown).
- If the printer connections are deployed per-user, go to User Configuration, Policies, Windows Settings, Scripts (Logon/Logoff).
- If the printer connections are deployed per-computer, go to Computer Configuration, Policies, Windows Settings, Scripts (Startup/Shutdown).
-
Right-click Startup or Logon, and then click Properties.
-
In the Startup Properties or Logon Properties dialog box, click Show Files. The Startup or Logon window appears.
-
Copy the PushPrinterConnections.exe file from the %WINDIR%\System32 folder to the Startup or Logon window. This adds the utility to the GPO, where it will replicate to the other domain controllers with the Group Policy settings.
-
In the Startup Properties or Logon Properties dialog box, click Add. The Add Script dialog box appears.
-
In the Script Name box, type: PushPrinterConnections.exe
-
To enable logging on client computers running Windows Server 2003, Windows XP, or Windows 2000, in the Script Parameters box, type: –log
Log files are written to %WINDIR%\temp\ppcMachine.log (for per-computer connections) and to %temp%\ppcUser.log (for per-user connections) on the computer where the policy is applied.
-
In the Add Script dialog box, click OK.
-
In the Startup Properties or Logon Properties dialog box, click OK.
-
Use GPMC to link the GPO to other OUs or domains to which you want to deploy the PushPrinterConnections.exe utility.
Wednesday, July 15, 2009
no more connections can be made to this remote computer at this time
1. Click Start, click Run, type regedit, and then click OK.
2. Locate and then click to select the following registry subkey:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\Lanmanserver\Parameters
3. On the Edit menu, point to New, and then click DWORD Value.
4. Type MaxMpxCt, and then press ENTER.
5. Right-click MaxMpxCt, and then click Modify.
6. In the Value data box, type the desired value, and then click OK.
Note You can set the number of concurrent SMB commands to a value that is between 10 and 255. The default value is 10. In Microsoft Windows Server 2003, you can set the number of concurrent SMB commands to a maximum value of 65,535.
7. Close Registry Editor.
Default XP Professional conncurrent connection is 15.
Thanks Microsoft
Wednesday, June 3, 2009
your current security settings do not allow you to download from this location
2. Click Tools, and then click Internet Options.
3. In the Internet Options click the Security tab.
4. Click Local intranet, and then click Custom Level.
5. Under Reset Custom Settings, click Medium in the Reset to list.
6. Click OK two times.
same above settings to Internet Security tab.
Wednesday, May 27, 2009
AutoUpdate time with EPO
It's time can be changed by the local user, but there's a better way if you want to manage when updates occur from ePO....
Within the User Interface policies is a checkbox: 'Disable default Autoupdate task schedule'. if you check this box, when policies are applied, the local AutoUpdate task is disabled (it can't be removed from the list). However you must also setup your own update tasks, and schedule them.
(I suggest you do this first and make sure they are working before disabling the default AutoUpdate)
You can have greater control this way, so that (for example) you can check for DAT updates each hour, Engine updates (via a seperate task) each day, patches once a week and so on....
hope that helps.